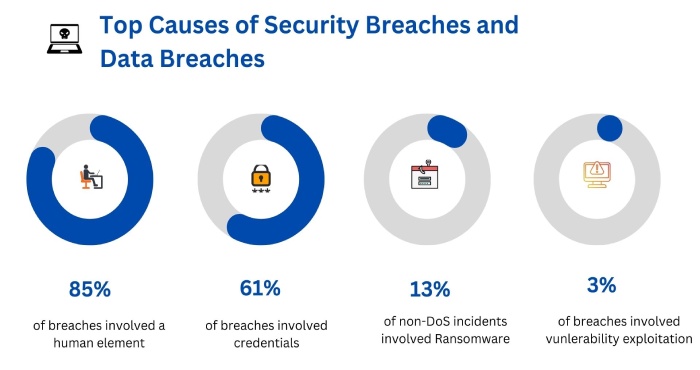
UK Defence Payroll Breached, Wichita Ransomware Pause, Lockbit Teases Reveal - Cybersecurity News [May 06, 2024]
Here’s our latest cybersecurity news piece that will show you how to keep yourself safe from all the new tactics of cybercriminals and what’s going on in the digital security space. Join us, and we’ll share how the UK Ministry of Defence’s payroll data was compromised, why Wichita had to halt its IT network operations, the new details about LockBit and its potential return, NSA’s alert on North Korean threat actors misusing DMARC policies for spear phishing and intelligence exfiltration, and the data compromise of 800K individuals by the University System of Georgia.
UK Ministry of Defence Payroll Data Compromised in Security Breach
The UK Government confirmed news that a threat actor was able to breach its Ministry of Defence.
The threat actor gained access to the Armed Forces payment network that contains personal data of both active and reserve personnel, and also some recently retired veterans. Once they identified the attack, the MoD isolated its system to prevent further intrusion by the threat actors and also stopped all the payments. The salaries were not stopped, and soldiers were paid normally for April but the names, bank details, and addresses of nearly 270,000 military personnel were exposed during the attack.
The investigation is ongoing, but it has yet to be determined exactly how the breach occurred. The Defence Secretary, Grant Shapps, shared that evidence of “potential failings” has been found on the contractor’s side-which could have been the reason behind the breach.
There haven’t been any indications of the threat actors actually stealing the data but all affected personnel have been informed.
Wichita Halts IT Network Operations Following Ransomware Incident
The largest city in Kansas-Wichita, was forced to shut down many of its network operations as a result of a ransomware attack.
The city has been highly transparent and confirmed that they were the victim of a ransomware attack on 5 May 2024. Many of its IT systems were encrypted with it. Wichita shut down its computer network to control the spread of the malware and is conducting a thorough review of the attack. The city has not confirmed if any data was stolen, but it is most likely that the threat actors stole some. Many of the city’s payment systems still need to be fixed, and people are unable to pay for basic things like water bills, court citations, and tickets.
The first responders are still providing all services. And the city has also reported the incident to local and federal law enforcement agencies that are assisting to find out the threat actors behind the attack and how big the incident actually is.
Lockbit Resurfaces Online, Hinting at Upcoming Announcements on Police Actions
The NCA, FBI, and Europol seized a new ransomware data leak site that could hint at the return of the threat actors.
Back in February, a coordinated law enforcement effort called Operation Cronos disrupted LockBit’s operations. They seized servers, stolen victim data, and even retrieved decryption keys. Law enforcement took over one of LockBit’s data leak sites and used it to share information about the operation, including exposed affiliates and how LockBit doesn’t always delete stolen data after receiving ransom payments.
They also teased a reveal about the identity of LockBitSupp, who is believed to be a key operator. However, the reveal was underwhelming, simply stating they knew who LockBitSupp was but provided no details. This was seen as a misstep by law enforcement. Now, they have revived the LockBit site with seven new blog posts scheduled for release.
The titles hint at potential reveals about what law enforcement has learned and info about more LockBit affiliates. Most importantly, they might take another attempt to answer who LockBitSupp is. Though the threat actors have been weakened by the takedown, LockBit is still launching attacks and remains a threat to businesses.
NSA Issues Alert on North Korean Cyber Groups Targeting Inadequate DMARC Email Security
The National Security Agency (NSA) and FBI have warned that North Korea-linked hacking groups are exploiting weak DMARC policies to mask spear phishing attacks.
Domain-based Message Authentication Reporting and Conformance (DMARC) is an email authentication protocol that helps you verify if an email is legitimate by checking if it is actually coming from the domain it claims to be from.
It helps prevent attackers from spoofing email addresses. The threat actors are abusing misconfigured DMARC policies and sending spoofed emails to think tanks, research centers, universities, and media organizations.
The hacking group linked to North Korea’s Reconnaissance General Bureau (RGB) is APT 43, which steals data and gains intelligence on geopolitical events, foreign policy, and topics relevant to North Korea. They send spear phishing emails impersonating journalists and academics and exploit poorly configured DMARC policies to gain intelligence and supply it to North Korea.
The threat actors can exploit domains with missing DMARC policies or the ones that have their policy set to none. If you want to stay safe, you need to change your policy to quarantine or reject so suspicious emails are quarantined or blocked altogether.
800K exposed in 2023 MOVEit attack on the University System of Georgia
This week, the University System of Georgia (USG) sent data breach notifications to nearly 800,000 people whose data was exposed in the Clop MOVEit attacks it suffered in 2023.
The USG oversees 26 public universities in Georgia and was hit by a breach in late May 2023 when threat actors leveraged a vulnerability in the file transfer software used by USG. The breach affected students, staff, contractors, and other affiliated personnel and was reported to the authorities.
The FBI and CISA helped the USG, and they recently shared that Clop made away with sensitive files from the systems, which included their full or partial Social Security Numbers, birth dates, bank account numbers, and federal income tax documents. The Clop ransomware gang exploited a zero-day vulnerability in Progress Software’s MOVEit Secure File Transfer solution, which allowed them to steal the files.
USG is now offering 12 months of free Experian identity protection and fraud detection to the people impacted by the breach and you can enroll if you were affected by 31 July this year.