Cyber Security vs Ethical Hacking: What’s the Difference?
Are you struggling to safeguard your organization’s data from the plague caused by malicious attacks such as spoofing, DDoS, phishing, malware, etc.? In your pursuit of a secure and resilient future for your organization, we are sure you must have come across the term “cyber security strategy” quite often! Do you think it is just another buzzword, or does it carry real significance?
Spoiler alert: it does! Cybersecurity strategy involves so much more than simply implementing technical defenses; it also involves playing the opponent’s cards. These approaches can be broadly classified as cyber security and ethical hacking, respectively.
Cyber security and Ethical Hacking are two sides of the same coin, each essential and complementary to the other in creating a robust cybersecurity strategy. In this article, we will decode the basics of cyber security and ethical hacking and learn what sets them apart.
What is Cyber Security?
Cyber security, as a concept and strategy, is as simple and complex as you can fathom. Let’s decode what we mean by this statement.
As a concept, it simply means doing all that you can to protect yourself and your organization from nefarious attacks such as phishing, ransomware, DDoS, spoofing, and more. But why bother defending against such attacks?
The aim is simple: to ensure that all your confidential and sensitive information, such as emails, critical business data, and bank details, remains away from the prying eyes of cyber attackers.
At its core, cyber security is about building a secure and resilient digital environment where individuals and organizations can go about their work safely and with confidence without having to worry about someone sneaking into their digital space to steal or damage their valuable information.
As a strategy, cyber security involves resorting to a comprehensive range of solutions to fulfill the aim of preventing threat actors and attackers from trespassing on your systems and network and causing a riot. Now coming to what goes behind the scenes of safeguarding your digital infrastructure, it involves implementing a multi-layered defense plan that includes a mix of technological solutions, rigorous processes, and human vigilance.
Some of the key pillars of this domain include:
- IoT Security
- Identity Management
- Application Security
- Network Security
- Information Security
- Cloud Security
- Endpoint Security
- Mobile Security
What is Ethical Hacking?
Have you heard the Greek maxim “Know Thyself”? This is a simple yet profound statement, which means that “knowing oneself is the gateway to wisdom.” It can also be applied in almost every context, including cyber security.
Wondering how? Let’s break it down for you!
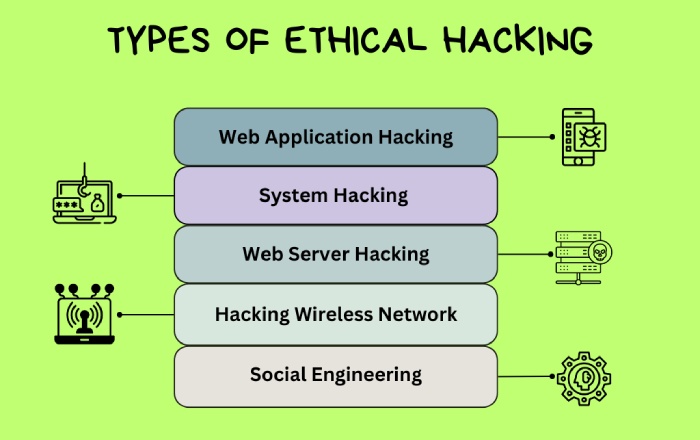
Ethical hacking, like the Greek principle, involves understanding the vulnerabilities and strengths of your entire digital infrastructure, including computer systems, networks, and applications. Its goal is to build a solid line of defense against cyber threats. But how is it done, and who executes it?
Unlike hacking, which is pulled off with malicious intentions, ethical hacking is a strategic approach followed by ethical hackers or white hats. This form of hacking is carried out with due permission from the owners of the systems, using the same tools and techniques as black hat hackers, but with an aim to detect and report vulnerabilities instead of exploiting them. Platforms like Pentest-Tools.com support ethical hackers by providing automated tools for reconnaissance, scanning, and vulnerability assessment, crucial steps in identifying and mitigating security risks.
Reminds you of the approach: think like the adversary to beat the adversary, right? By thinking like the adversary (cyberattacker), weak points within computer systems and networks that might otherwise go unnoticed. All of this effort boils down to one thing— anticipate how a malicious hacker could potentially breach a system and patch loopholes before the threat actor is able to do so.
As you might have guessed, ethical hacking is a critical component of cyber security that relies on a five-phase approach—
- Reconnaissance: Gathering information and data from sources like the target’s network, social media, websites, etc.
- Scanning: Using automated tools to actively probe the target for specific vulnerabilities.
- Gaining Access: Exploiting vulnerabilities to gain unauthorized access to the system or network.
- Maintaining Access: Maintaining presence within the system without being caught with an aim to understand the potential risks.
- Analysis and Reporting: Leveraging all the information gathered to create a detailed report.
What is the Difference Between Cyber Security and Ethical Hacking?
Now that we have a basic understanding of each concept, let us look at how they are different from each other.
| Measures | Cyber security | Ethical Hacking |
| Basic Premise | Protecting systems and servers against attacks and unauthorized access to create a secure and resilient environment | Looking for specific vulnerabilities in systems or networks and to gain insights into how they can be exploited |
| Scope | An all-encompassing scope that involves prevention, detection, and response to threats. | Specifically focuses on gaining access into the system to identify security weaknesses. |
| Approach | Implementing authentication policies, like SPF, DKIM, and DMARC, firewalls, antivirus, encryption, etc. | Conducting penetration tests, vulnerability assessments, and security audits |
| Outcomes | A safe and resilient digital ecosystem where the risk of threats is minimized and managed effectively | Detailed reports on vulnerabilities and recommendations for strengthening security |
Since cyber security and ethical hacking are so closely related, does that mean we can use the two concepts interchangeably? Unfortunately, no! Looking at the broader picture, yes, they work towards the same goal, that is, keeping digital spaces safe. However, they do different things and can’t simply replace each other. What you can do is leverage the synergy between the two to increase the robustness of your digital defense strategy.
Want to integrate state-of-the-art approaches into your cyber security strategy? DuoCircle is your ally! At DuoCircle, we understand that cyber security and ethical hacking play unique but complementary roles in keeping our digital world safe. This is why we are here to give you the best of both worlds— comprehensive protection with proactive testing.
For instance, our PhishProtection Simulator can help you and your team learn how to identify and tackle phishing emails while providing a comprehensive insight into your team’s tendencies to respond to such emails.
Want to learn more about how you can leverage our services to protect your critical data? Get in touch with our team, or book your demo today!