The LAPSUS$ gang has claimed responsibility for a breach in tech giant Microsoft and Okta, an organization that provides authentication services for networks of FedEx, Moody Corp, and many prominent organizations. The breach was identified on March 22, 2022, with organizations still uncovering the scope of the breaches. But there is a certainty that a severe threat is looming over both organizations and their customers. Here is a comprehensive summary of the event of the breach.
The Microsoft and Okta Breach At a Glance
LAPSUS$ group shared sensitive screenshots and the source code of Microsoft and Okta’s internal projects on Telegram. The stuff leaked by the cybercriminal group comprises a 37 GB archive, showing their access to Microsoft’s Bing, Maps, and Cortana. Furthermore, the leak also featured a statement by the hacker group condemning the security measures of Okta, a service provider with thousands of clients worldwide, accompanied by screenshots of Okta’s sensitive accounts, such as Cloudflare, its Atlassian suite, and many in-house channels.
Impact on Consumers
The LAPSUS$ group, also known as DEV-0537, clarified that the cybercriminal group is focused on Okta customers and not its databases, revealing a significant threat to Okta consumers. Cloudflare highlighted how it had not been compromised, with FedEx stating that it is carrying out an investigation that has not revealed any signs of compromise or access yet. Okta has also issued statements claiming only 2.5% of customer accounts were potentially impacted but has sparked controversy as LAPSUS$ is accusing Okta of undermining the importance of the breach.
Microsoft customers have not been affected yet but have received a complete security blog by Microsoft, highlighting the criminal group’s threat and providing customers better information on threat detection, hunting, and mitigation to stay vigilant and protect themselves better. LAPSUS$ has only exfiltrated portions of Microsoft’s source code. Microsoft highlights how there is no secrecy of code or elevated risk to its customers as the threat actor was stopped mid-operation, preventing the broader scope of the breach.
What is LAPSUS$, and Why Should Customers be Wary?
The LAPSUS$ is a group of cybercriminals targeting large organizations for data exfiltration and extortion. The group emerged in December 2021 and has since claimed responsibility for various cyberattacks in a bid to steal confidential information and demand money. The list of LAPSUS$ targets includes:
- Compromise of Brazilian Ministry of Health’s COVID database.
- Breaches of Claro, Embratel, and NET.
- Theft of proprietary data from NVIDIA and Vodafone.
- Theft and leak of source codes for authentication, bootloaders, and DRM from Samsung.
- Disruption of games and services of Ubisoft.
- Theft of user and service account credential hashers of LG Electronics.
- And the latest LAPSUS$ breach involving the theft of Bing, Bing Maps, and Cortana from the internal Azure DevOps servers of Microsoft.
How did LAPSUS$ Breach Microsoft and Okta?
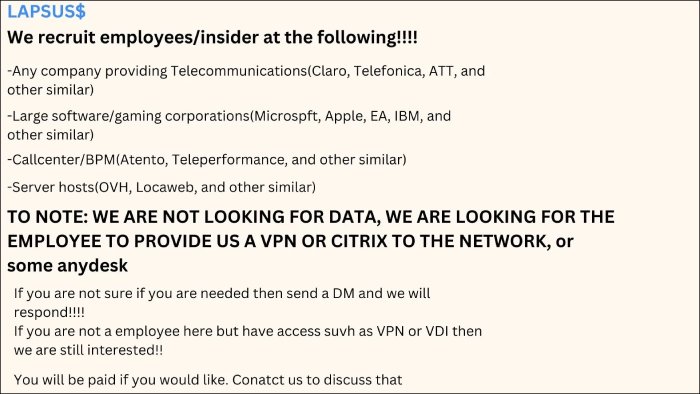
LAPSUS$ is known for its unique attack pattern of using extortion and destruction to demand money without the need for ransomware. Furthermore, LAPSUS$ is also infamous for recruiting employees as insiders to gain access to the internal networks of various organizations in the hardware, software, gaming, and telecommunications industry. The following image shows a message from the group’s hacker channel revealing a cybercrime job posting for insiders.
DEV-0537 has a unique approach following these steps:
Access to Networks: The cybercriminal group uses social engineering tactics to gather employees, help desk, attack response flow, and supply chain information. It then uses various techniques to compromise user accounts using Redline password stealers, purchasing login credentials, recruiting insiders, and public repositories for exposed login information. Once DEV-0537 has the credentials, it starts the next phase of its attack.
Monitoring: Using the account credentials, LAPSUS$ gains access to an organization’s network and monitors the environment, exploiting GitLab and JIRA vulnerabilities on internal servers to uncover additional credentials and intrusion points for gaining access to higher privileged accounts. Understanding how to export data from Jira can help security teams analyze activity logs more effectively and identify suspicious behavior patterns.
Exfiltration and Extortion: LAPSUS$ is highly skilled, able to avoid sophisticated detection techniques, and quietly exfiltrates target data for the purpose of extortion. LAPSUS$ uses NordVPN access points with dedicated VPS (virtual private servers) to gain access to cloud tenants such as AWS or Azure. It then creates global administrator accounts for gaining control and eliminating other administrator accounts and often erases the stolen data or resources from the organization’s cloud after exfiltration.
How Can Customers and Organizations Strengthen Account Security Against Such Cyber Threats
There are various techniques and security protocols that customers can follow to strengthen their account security and shield themselves against the threat of the LAPSUS$ breach, such as:
Enable MFA: You must enable MFA as it is the first line of defense against such threats; you can employ Azure password protection, utilize automated reports, enable MFA for all users and locations, and implement risk-based policies.
Endpoint Management: Data theft can be prevented to a significant extent by allowing only trusted and compliant devices to access resources. Besides, encourage the use of tools such as Microsoft Defender’s cloud protection to block new and unknown malware.
Social Engineering Awareness: DEV-0537 uses social engineering tactics to manipulate employees to gain access to credentials and the internal network. Educating yourself and your employees to identify common social engineering tactics and reporting unusual contacts can significantly improve the organization’s cyber posture.
Final Words
The latest data breach on Microsoft and Okta by DEV-0537 is a prime example of today’s sophistication and ever-transforming cybersecurity threats. When giant corporations and service providers are breached, it is highly likely that the organizations that use their services will soon be impacted by the breach, directly or indirectly. Organizations need to implement the best email security methods, employ basic cyber hygiene practices, and comprehensively assess internal risks to mitigate them and better protect their organization and customers.