Understanding the ins and outs of attack simulations
Attack simulation is a cybersecurity technique that tests defenses by imitating tactics, methods, and procedures used by threat actors to exploit vulnerabilities and launch attacks. Its purpose is to spot system vulnerabilities and help the security team remediate them before someone capitalizes on them for malicious purposes.
The concept of attack simulation is similar to penetration testing, but the former helps you understand how attackers might navigate your defenses and if the existing security operations are resilient enough against those strategies.
Let’s get into the detail of the topic.
What is an attack simulation?
Attack simulation involves emulating a full attack cycle on an organization’s network, infrastructure, and assets using real-world attacker tactics and techniques. These simulations can focus on specific threats like malware, ransomware, or vulnerabilities and may include security teams to evaluate their response.
The goal of attack simulation is to assess how well security controls and teams detect and mitigate attacks, uncover vulnerabilities, and identify areas needing improvement. By regularly testing from an attacker’s perspective, organizations can strengthen their defenses and reduce risks caused by misconfigurations, vulnerabilities, or risky user behavior.
The attack simulation tools are highly automated, enabling frequent tests compared to the longer gaps seen in traditional penetration tests or red/blue team exercises. This frequent testing provides better visibility into an organization’s true security state, aligning with the principles of Continuous testing, where automated and ongoing assessments help organizations quickly identify and address vulnerabilities as they arise.
6 steps of an attack simulation
The simulation should be planned and performed strategically for optimum outcomes and to ensure that you don’t harm the system. The attack simulation process typically unfolds in 6 steps–
Threat profiling with cyber threat intelligence
The foremost step is to diligently understand the organization’s security structure and attack history. For example, if your company belongs to the finance sector, you should consider researching cyber threats and advanced persistent threat (APT) groups that often target this sector.
Defining the attack simulation scope
Next, specify the scope of your cyberattack simulation. Start by establishing boundaries so that you work in a controlled environment, ensuring that not all your operations are disrupted. Defining the scope not only validates the effectiveness of security controls but also improves response times because the person in charge of cybersecurity gets familiar with the infrastructure and its complexities.
Defining the objective of the cyber attack simulation
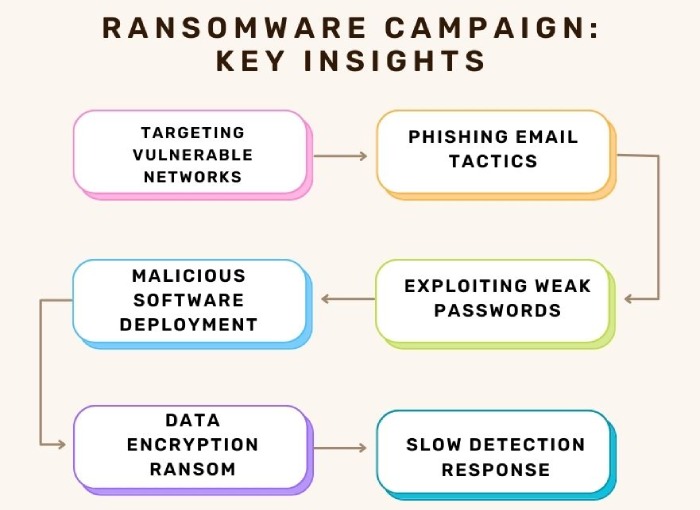
Every attacker has a specific goal, whether it’s financial gain, recognition, or activism. Their aim is to maximize the impact of their attacks. For instance, in a ransomware campaign, attackers seek the highest privileges to infect as many systems as possible, forcing victims to pay to restore operations and secure sensitive data.
Similarly, when planning an attack simulation, offensive security professionals must define clear objectives. These might include accessing the domain controller, compromising a domain admin’s account using credential-dumping techniques, or other specific targets.
Planning the attack
This stage involves carefully outlining the potential attack pathways while also considering the company’s unique threat landscape and identified objectives. In this step, security personnel also determine the tools to be used for simulation. These tools can belong to third parties or be native operating system utilities.
It’s important to enlist a variety of cyberattack techniques. Common ones include malware injection, exploitation of SPF, DKIM, and DMARC misconfigurations, network reconnaissance, etc. This planning phase turns the simulation’s goals into a clear, actionable plan, ensuring an effective cyber attack simulation.
Executing the cyber attack simulation
While executing the attack simulation, the offensive security professionals carry out the strategized plan. They consider the strategy laid out in the previous step as a guide; however, they keep the process relatively flexible to adapt to unexpected opportunities.
For instance, during reconnaissance, they might discover a privileged user account with access to critical domains. If they gain unauthorized access, they could exploit this to access a domain controller or sensitive servers, such as those hosting financial records.
This adaptability ensures the simulation effectively uncovers vulnerabilities, making it more accurate and thorough.
Results and reporting
Once the attack simulation is done, the offensive security professional develops a detailed report on how the process was conducted, what all vulnerabilities were spotted, and what remediation actions are to be taken.
The comprehensive report is like an actionable guide that helps the organization understand the effectiveness and resilience of its security defenses. By filling the gaps, owners can make their technical infrastructure attack-proof.
The way forward
This cybersecurity technique runs on automation and provides real-time feedback. It can be made to run continuously or as required without appointing more human resources. It leverages frameworks like MITRE ATT&CK and integrates with SIEM/SOAR tools.
Once you have worked on the suggested remedial and gaps are filled, ensure the next round of simulation shows improvements and progress. Reach out to professionals for the best help— DIYing isn’t always a good choice.