The 7 Stages of a Typical Cyberattack
Cyberattacks have become a grim reality of our digital world, with each attack increasingly sophisticated, targeted, and damaging than the last! Every click, every download, and every seemingly harmless online interaction has the potential to let in uninvited guests [read: cybercriminals] who can wreak havoc on your digital infrastructure in ways you cannot imagine.
Even if we assume that the defense mechanism of your organization is way too strong to allow any threat actor to come near you, the way in which cybercriminals operate negates this perception. The thing is, cybercriminals are not picky; they’re opportunistic, and the moment they spot any vulnerability, they exploit it, regardless of where it is or whom it affects. This is precisely why the number of people who got hacked in 2023 alone reached up to 343 million!
If cybersecurity threats are so pervasive, how do you ensure a safe and secure digital environment for your organization? Understanding how attackers orchestrate their moves can empower you to better protect your online digital assets and systems.
In this article, we will take you through the seven stages of a cyberattack and delve into what happens ‘behind the scenes’ at each phase. With this knowledge in hand, you can better comprehend, anticipate, and mitigate potential threats.
What are the Stages of a Cyberattack?
Reconnaissance
Did you know that attackers don’t target just about anyone they come across; rather, they are very strategic in identifying the ideal target? As you might have guessed, they scout as much information as they can about their potential targets. This includes meticulously gathering information about prey, recognizing its vulnerabilities, and even identifying any third-party connections that may provide an indirect route to their main target.
From simple internet searches to deploying sophisticated tools such as network scanning technologies to uncover vulnerabilities, the attackers go all the way to find dirt on you!
Weaponization
After digging deep into the target’s profile in the reconnaissance phase, the perpetrators move on to the weaponization phase.
Remember the loopholes and vulnerabilities found in the first stage? This is where they put all of it to use! The attackers leverage the information gathered to tailor tools that will hit right at the Achilles heel of the intended victim.
To execute their nefarious intentions, the attacks might go as far as crafting a new type of malware or tweaking existing ones to better suit their needs; this phase is all about perfecting the means of attack. For instance, the attacker might take the existing malware variant and modify it to evade the specific antivirus software used by the target. Or perhaps, develop an entirely new exploit that the victim’s system is unequipped to tackle.
Delivery
The next stage of a cyberkill chain is the delivery phase. In this phase, the cyber attacker deploys the weaponized payload created in the previous phase into the target’s digital environment. By resorting to methods like phishing emails, direct network exploitation, compromised websites, and social engineering, the attacker ensures that the ransomware reaches the intended system without getting detected along the way. Once the payload is successfully delivered to the target’s system, it begins to unload itself within the environment, setting the stage for the next phase.
It is crucial to understand that without successful strategic delivery, the entire attack could falter.
Exploitation
After a successful breach in the previous phase— the delivery phase, the exploitation phase is where the real damage happens! Once the cyber attackers identify the target and launch their bullets into the target’s system, the downfall begins. During this phase, the adversaries enter the victim’s system and move laterally across it to gain a deeper understanding of the user’s infrastructure with information like how it operates, what the traffic flow looks like, etc.
Installation
The installation phase of the cyber kill cycle involves maintaining continued access to the target’s system. To ensure that the breach is deep and lasting, the attacker takes deeper control of the system by turning off any firewalls, gaining administrator access, and locking the users or other devices out of the system.
Moreover, the primary goal of this phase is not to enter the system but to maintain a secure connection within it, which can also be done by triggering remote desktop access on servers or devices.
Command and control
As soon as the hacker manages to get full access to the target’s system or network, they work towards taking control of the latter’s infrastructure. Taking control, here, implies that the attacker does everything in their capacity to manipulate and exploit the information stored in the system. To avoid getting caught, they do it all in the garb of a trusted entity authorized to carry out these tasks.
Action on Objectives
This is the final stage in the lifecycle of a cyberattack. In this phase, the attackers achieve what they came in for—stealing sensitive information, causing operational disruption, and demanding ransom, among other activities devised to fulfill their malicious intent.
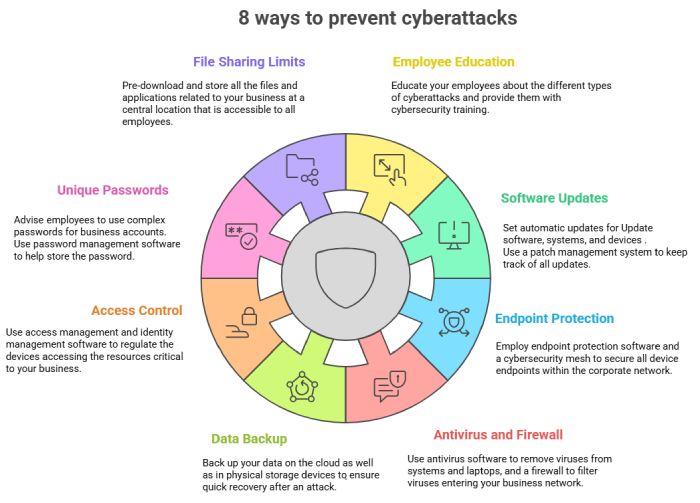
How Can You Stop this Cycle?
This is not a rhetorical question but a pertinent one that you must address to ensure that all your online endeavors are safe and secure.
Here’s how you can break this vicious cycle:
Implement Robust Security Measures
To get ahead of the attackers, it is crucial to have a game plan in place and, most importantly, to implement it! Apart from deploying security solutions like firewalls and antivirus software, you can up your email security game with email authentication protocols like SPF, DKIM, and DMARC.
Limit Privilege Access
Not everybody deserves to have privileged access to your system. To avoid security risks and insider threats, keep the access limited to only those necessary for performing job duties.
Regular Security Audits and Assessments
Keep an eye on what is going on in your organization’s digital environment by conducting regular security audits and assessments. Doing this will reveal any loopholes in your security system and help you strengthen your defenses.
If you are concerned about being a victim of a grave cyberattack, the time to act is now! Get in touch with our team of experts at DuoCircle and learn how we can work together with your security team to keep cyberattacks at bay!