Phishers abuse Google sites and DKIM replay to send fake emails and steal credentials
The email message informed the targeted recipients of a subpoena from a law enforcement authority, querying about unspecified content in their Google Accounts. The message further urged them to click on a malicious link on the false pretext of examining the case materials or taking measures to submit a protest.
The malicious link redirected recipients to a cloned, look-alike webpage that impersonated Google’s actual Support page. There, the victims were requested to click on a button to upload documents or view the details of the case.
The tricky part of this attack was that the email showed that it was ‘Signed by’ accounts.google.com, even though it was actually sent from a completely different domain: “fwd-04-1.fwd.privateemail.com“.
Here is what the message looked like-
The role of DKIM replay in this attack
In this attack, the threat actor cleverly manipulated DKIM authentication to make a phishing email appear fully legitimate.
The process began with the attacker creating a Google account using a newly registered domain (like me@<domain>). They then set up a Google OAuth application, naming it in a way that mimicked the entire phishing message. After granting their OAuth app access to the Google account they just created, Google automatically generated a security alert email to that same account.
Since Google created and sent the alert, the email was signed using Google’s valid DKIM key, meaning it passed all DKIM, SPF, and DMARC authentication checks.
The attacker then forwarded this exact message from an Outlook account but carefully preserved the original DKIM signature. By doing this, the email retained its ‘Signed by Google’ authenticity, even though it was now being sent from an unrelated domain.
To further obscure its path, the message was routed through a custom SMTP service, eventually relaying through a mail-forwarding infrastructure. By the time it reached the target’s Gmail inbox, it looked like a genuine message from Google — complete with clean authentication results. This significantly increased the chances of the phishing email bypassing filters and tricking the victim.
What Google says about this
Google has acknowledged and confirmed the attack and has already started taking action to ensure this doesn’t continue to happen. The officials have come forward to explain how they are aware of these kinds of targeted phishing attacks and that they have taken the appropriate measures to shut them down.
They have also reiterated that Google never requests sensitive details from users, including one-time passwords, and neither do they call to ask for such information. Google prioritizes user security and encourages people to stay vigilant online.
As an added layer of defense, Google is urging users to enable two-factor authentication (2FA) and adopt passkeys — both of which offer stronger protection against phishing attempts like these.
How can businesses prevent DKIM replay attacks from their domains?
DKIM replay attacks are very tricky and sophisticated, and with the advent of AI, it’s easier to draft convincing and flawless phishing emails. If these emails bypass security filters, the chances of a successful phishing attack increase. But businesses can still prevent their domains from getting involved in DKIM replay attacks. Here’s how-
Use DKIM with short-lived signatures
Set a short expiration time (x= tag) in your DKIM signature. Doing so reduces the window for a threat actor to use a key repeatedly for malicious purposes. So, even if your domain gets involved in a replay attack, it won’t be dragged for long.
Enable SPF and DMARC
If SPF is deployed, emails sent from unauthorized IP addresses are regarded as illegitimate and potentially phishing. That’s why they are either tossed in the spam folders or bounced back to the sender.
Now, unless the malicious actor is one of the insider threats, there is a chance their IP address won’t be a part of your SPF record. Hence, the replayed emails won’t pass SPF authentication and reach the targeted recipients’ primary inboxes. Note that it will only work if threat actors send the emails from your domain.
DMARC, on the other hand, works based on SPF and DKIM results and directs receiving mailboxes on handling emails that don’t pass SPF and/or DKIM checks.
Regularly rotate DKIM keys
If you frequently rotate your DKIM keys, then the stolen keys become stale soon. This way, threat actors can’t keep exploiting them for an extended period. Also, ensure that you securely store and manage your keys.
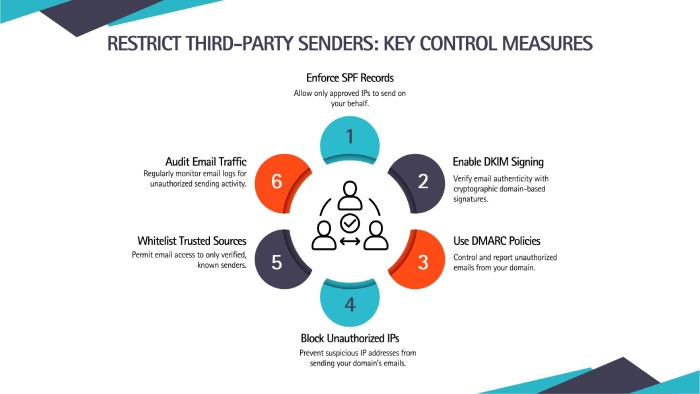
Restrict third-party senders
If you engage with third-party services to send emails on your behalf, it’s important that you ensure they have proper email authentication protocols in place. Also, make them follow the best practices to manage DKIM keys so that they don’t leave them exposed to misuse.
Monitor DMARC reports
Enable DMARC monitoring in your DMARC record. Doing so helps you receive detailed and insightful reports on all the emails sent from your domain. Look for unusual patterns, spikes in forwarded messages, and unidentified IP addresses. All of these indicate malicious email attempts.
We at DuoCircle can help you get started with DMARC reporting if you haven’t already. So, contact us and see how things work.