The reports of the past five years show that around 80% of all cyber-attacks are impersonating social engineering attacks. Today, most email attacks are malware-less to avoid setting off malware scanning alarms. The primary aim of adversaries is to gain the target’s trust by impersonating some legit entity or user. As the emails do not contain any malicious content, they can easily bypass the email security defenses.
The situation has even worsened globally during pandemic times as most of the phishing attacks are coronavirus-themed. Malicious actors take advantage of the employees working from home with less secure connections and endpoint devices.
Malicious attacks are becoming so sophisticated that even Google has reported that 68% of phishing attacks are unheard of before. The traditional phishing protection and anti-phishing services are not sufficient as malicious actors in their more sophisticated gambit have automated phishing to avoid detection.
Hence, the time has come to switch from traditional email security measures to a more comprehensive IT security architecture, the Zero-Trust model.
Understanding Zero-Trust Model
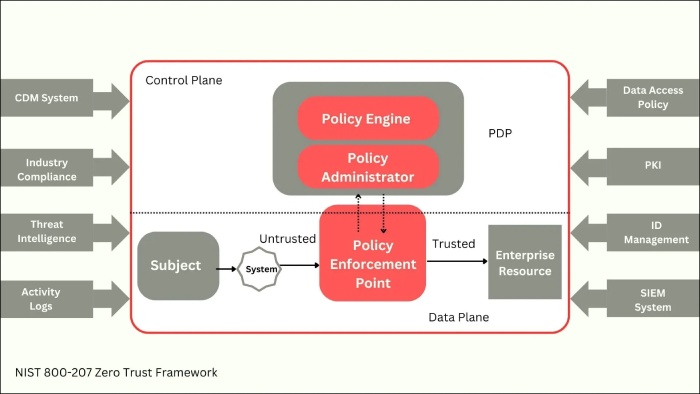
As the name suggests, Zero-Trust is a security framework that assumes no trust at all. It treats every internal or external user requesting access to the organization network as a potential threat. This security model requires the users’ continuous authentication, authorization, and validation by using multiple security measures and critical controls before granting access to any data, application, or information system.
The framework makes use of a combination of advanced technologies, such as
- Multi-Factor Authentication,
- Identity and Access Management (IAM),
- Identity Protection, and
- Next-generation endpoint security to verify the identity of the user and to maintain system security.
Zero-Trust architecture marks the departure of the traditional network security approach of “trust but verifies” that trusts the users within the organization. Such a conventional method can put the entire organization at risk from internal factors. If some of the internal accounts get compromised, an external adversary may access the organization’s complete array of data, sites, applications, and devices.
The Zero-Trust model is here to deal with this flaw, which assumes that the network has already been compromised. It continuously monitors and validates every user by asking them to prove that they are authorized, whether internal or external entities.
As one-time validation does not suffice, multiple security and identity verification measures are put in place for users and their devices attempting to access the network, even when they are internal entities.
Why Is There a Need to Employ Zero-Trust Architecture For Email Security?
The Zero-Trust architecture redefines email security by authenticating each user. In essence, a user cannot deliver a message to the receiver’s inbox unless authenticated. The model ensures that only the genuine sender is granted explicit permission to send the email.
Email scammers mutate their identity rapidly, making it challenging for AI/ML solutions to identify it. The content-centric solutions only work effectively in identifying malicious content and social engineering trends, making the network vulnerable to identity-based attacks.
Hence, to patch this vulnerability, the Zero-Trust email security model focuses on identifying trustworthy senders. On employing this approach, emails not in the trusted sender’s list will get automatically red-flagged and get blocked or treated as spam.
Guiding Principles Behind Zero-Trust Architecture
The following are the salient principles that constitute the Zero-Trust architecture.
- No one is trusted: As the attacker can be either inside or outside the network.
- Privileged access is limited: The user only gets access to the required extent and not more. It ensures limited exposure to sensitive data.
- Micro-segmentation: This means breaking the whole security perimeter into small zones, and each zone will have separate access.
- Establishing Multi-factor Authentication (MFA): The requirement of more than a piece of evidence for the user’s authentication, easily manageable via platforms such as Descope.
- Establishing control over device access: Closely monitoring which device is trying to access the network and whether it is authorized or not.
- Real-time monitoring of activities: To spot abnormalities, if any.
Benefits of Zero-Trust Model
By employing the Zero-Trust model, an organization can have various cybersecurity benefits. Here are the main advantages.
- By employing the Zero-Trust model, an organization can control access to their networks, data, devices, and applications.
- Prevents phishing and spear-phishing emails targeting the employees.
- Prevents any data breach and also contains lateral movement by making use of micro-segmentation.
- Offers phishing protection and email security across several computing environments, independent of the underlying infrastructure.
- Helps gain insight into various devices, users, components, as well as workloads across the organization.
- Enables continuous monitoring to detect and respond to any signs of compromise.
- Enables the user to control what happens to untrusted emails, i.e., they can decide whether to quarantine, delete, or monitor them.
- Employs multiple alerts, reports, and logs to promote threat detection.
- Provides a consistent user experience along with ensuring organizational security.
Final Words
Phishing attacks are becoming more and more sophisticated, and the cost of becoming a victim of it is already too high and getting worse by the day. The traditional phishing protection and anti-phishing services are unable to keep pace with the ever-evolving cyber-attacks. Therefore, it’s time to adopt the new and effective zero-trust framework to maintain email security. This new approach does not trust any user; it instead asks them to prove whether they are authorized to enter the inbox or not. On top of this model, one can also employ a filtering solution to ensure that no malicious email from a compromised account slips through. With the Zero-Trust Architecture in place, one can create an environment where the system can truly trust all the emails in the inbox.