Understanding the process and importance of hashing in DKIM
DKIM was created in 2005 to help recipients determine if someone has tampered with the email content in transit. The protocol is broadly based on the concept of cryptography, which ensures the authenticity and integrity of an email message by using a public key to sign the outgoing emails for your domain. In DKIM, hashing is an important step in creating a secure signature for email integrity and authentication. Let’s see how hashing works.
What is hashing in DKIM?
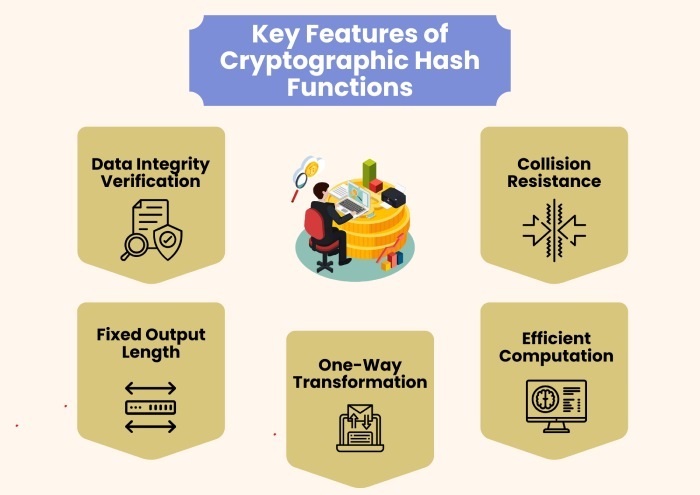
Hashing is responsible for converting a part of an email (typically header and body) into a fixed-size string of characters. These characters are usually a sequence of numbers and letters. This string is processed, and an output value is produced, which is called a hash value or digest. The same input always produces the same hash. However, if there is even a small change to the input, a completely different hash value will be produced. This makes hashing a one-way function, which means you can’t reverse it back to the original data.
How hashing unfolds?
Here’s a detailed step-by-step explanation of how hashing works within the DKIM framework:
Email headers and body selection
DKIM selects specific parts of the email to include in the signature, which includes email headers (e.g., From, To, and Subject) and the email body. This is done to create a verifiable fingerprint of the email’s content, ensuring that the message has not been tampered with during transmission.
Hashing the email parts
Once the headers and body are selected, DKIM hashes them using a cryptographic hash function. The commonly used ones are SHA-256 for RS256 and SHA-512 for RS512. While the former is the most common choice in DKIM, the latter provides a higher level of security.
Digital signature creation
After hashing, DKIM takes the hash (digest) and signs it using an RSA private key associated with the sending domain. This creates a digital signature, which is embedded in a special DKIM-Signature header of the email.
Verifying the signature using hashing
Upon receiving the email, the recipient’s server performs these three steps-
- Retrieves the public key from the sender’s domain’s DNS records.
- Hashes the email’s headers and body again, using the same hash function (SHA-256 or SHA-512) to generate a new digest.
- Verifies the digital signature using the sender’s public key, comparing the new hash (from the email body) with the hash in the DKIM signature. If the two match, the email is considered authentic and untampered.
Why hashing is important in DKIM?
Let’s see how hashing underpins the security and efficiency of email communication:
Integrity protection
Hashing plays a prominent role in ensuring the integrity of email content. The unique fingerprint created by hashing lets recipients know if anyone tried altering the email in transit—whether it was a minor change like modifying the subject line or something more serious and dangerous like embedding malware-infected links to the body text.
Here is why this matters-
Email tampering detection
Any change to the email content, no matter how small (even adding or removing a space), will cause the hash to change significantly. This means that the digital signature created from the hash is tightly bound to the exact content of the email at the time it was signed.
When the recipient’s server verifies the email, it re-hashes the content and compares it to the original hash stored in the DKIM signature. If even a single byte has changed, the hashes won’t match, causing the DKIM signature verification to fail. This prevents spoofing and instills trust in recipients, knowing that the email they received is exactly as the sender intended, with no alterations.
Protection from man-in-the-middle attacks
Without hashing, malicious actors can modify important information in the email content. For example, they can replace the original banking details with the ones belonging to them.
Immutable signature
Since the signature is based on the hash, it’s effectively ‘locked’ to the content at the time of signing. If anyone tries to change the content, they would also have to generate a new hash and a valid signature. This is impossible without the sender’s private key, which is securely kept by the sender’s domain. As a result, even if someone intercepts the email, they can’t forge a new valid signature to cover up their modifications.
Efficiency
Hashing contributes to the efficiency of DKIM in several key ways, especially when handling large volumes of emails.
Fixed-length output
Hash functions always produce a fixed-length output, regardless of the size of the input. For example, whether you hash a 10KB or 10MB email, the resulting hash is always a fixed-length string (e.g., 256 bits for SHA-256).
This simplifies and speeds up the process of signing and verifying emails. So, instead of dealing with the entire email message, DKIM only has to deal with a small, fixed-size hash when it creates or checks the digital signature.
It makes the process all the more efficient by making it easy to handle large emails because the computational effort required to generate and verify the signature becomes manageable as the hash value or digest is small and fixed-size.
Less data transmission
Since the hash value is smaller than the original content, signing and verifying emails become more lightweight. The recipient’s server doesn’t have to go through the hassle of directly re-verifying the entire email body. It only has to focus on hashing the email’s content and comparing the results to the signature.
It eventually decreases the load on both the sending and receiving servers, especially for high-volume environments like large email service providers.
Low overhead for high security
Hashing provides a high level of security without imposing significant processing or storage overhead. It’s a computationally efficient way to ensure security, making it well-suited to environments where performance is critical, such as email systems handling billions of messages.
One-way function
The cryptography hashing involved in DKIM is one-way, meaning it’s computationally infeasible to reverse-engineer the original input from the hash. This helps to ensure the following-
Irreversibility
Given a hash, recovering the original email content is nearly impossible. For instance, even if someone intercepts the hash value in the DKIM signature, they cannot reverse it to reveal the email’s content. This makes the hash safe to include in the DKIM signature, which is publicly available to anyone who receives the email. This ultimately disallows attackers from gaining any useful information from the hash.
Resistance to collision
Cryptographic hash functions like SHA-256 are designed to minimize the likelihood of collisions. This happens because two different inputs produce the same hash output. In practice, it’s extremely rare (and computationally infeasible) for different email contents to produce the same hash, which enhances the security of DKIM.
If a threat actor tries to alter the content and somehow produce the same hash (a collision), it would need multiple computational resources, which would add up to make the process impractical. This reinforces the security of DKIM.
Public key compatibility
As a one-way feature, hashing works well in tandem with DKIM’s public-key cryptography use. The hash is signed using the sender’s private key (which is kept secret), and the recipient verifies it using the public key (which is published in DNS). So even if the recipient has the public key and signature’s hash, they can’t reverse-engineer the original message or generate a valid signature for a tampered or altered email without having access to the private key.
Final words
The overall combination of security and performance makes hashing an essential element in the DKIM protocol, ensuring the reliability and safety of email communications across the internet. If you are still dubious about the efficacy of DKIM, reach out to us. We’ll help you make up your mind and get started with the email security and authentication process involving SPF, DKIM, and DMARC.