Decoding Canonicalization: The Reason Behind DKIM Signature Verification Failures
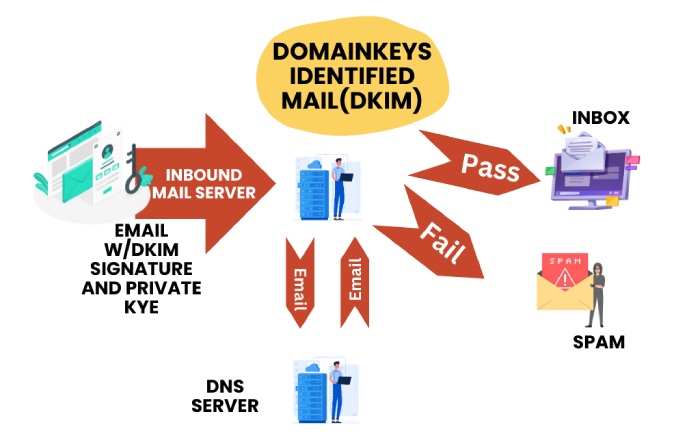
When you send an email to someone, it embarks on a complex journey before it reaches the recipient’s inbox. While this might seem like a seamless, instantaneous process, it is prone to being tampered with along the way. This is why it is recommended that you implement DomainKeys Identified Mail (DKIM) for your email communications.
If you enable DKIM for your outgoing emails, the receiving server checks them for any tampering that might have happened in transit by matching the DKIM signature generated using your private key with the public key published in your domain’s DNS record. If the private and public keys match, the email is considered good to go; if not, it might be raised as a red flag.
But the thing is, sometimes even legitimate emails fail DKIM authentication due to canonicalization issues, which ultimately jeopardize your domain’s email authentication.
In this article, let us dig deep into the issue of DKIM canonicalization and learn how we can resolve it.
What is DKIM Canonicalization?
To understand DKIM Canonicalization, we take into consideration the possibility that mail systems can sometimes alter the content of an email in transit. While these changes are not major (minute alterations like whitespace, line breaks, and case differences), they can hamper the integrity of the email and lead to DKIM failure.
However, with DKIM canonicalization, you can standardize the format of email headers and body before signing them with a digital signature. What we mean to say is that before an email reaches the recipient, its contents are transformed into a canonical form, a standardized version that is immune to alterations during transit. This ensures that the email reaches the recipient’s inbox exactly as the sender intended to send it in the first place.
Let us explain this through an example-
Consider the following email addresses:
- Johndoe@xyz.com
- Johndoe@XYZ.com
Given the formatting and case variation, it is very apparent that the two email addresses are different from each other. This discrepancy wouldn’t really matter when it comes to delivering email to the intended mailbox; they would deliver to the same mailbox. But when DKIM enters the picture, even the slightest alteration like this can pose a challenge.
This surely does impact your organization’s email authentication and deliverability efforts. Luckily, there are ways to remedy this situation and ascertain that DKIM signatures pass verification without canonicalization blocking the way.
How Can You Address this Challenge?
There are two canonicalization algorithms that you can leverage to address this challenge:
Relaxed Canonicalization
As you can tell by the name, this is slightly flexible as it gives you some wiggle room for minor alterations in the email content while still ensuring that the DKIM signature verification passes successfully. It removes any discrepancies found between the original email content and the transformed canonical form by:
- Removing any white spaces in the body
- Converting all header names to lowercase
- Ignoring spaces at the end of header fields
Simple Canonicalization
Simple Canonicalization is a little too simple to take into consideration the minor alterations that happen in an email during its journey from the sender’s outbox to the recipient’s mailbox. This means that this canonicalization algorithm follows the rule book to verify that the emails match exactly to the original content signed. It leaves no scope for even the smallest and seemingly most frivolous alterations like modified space or a new line break. If any discrepancies are found, the DKIM check will fail.
The stringent nature of simple canonicalization makes it complex and unfavorable. As you already know, certain changes and reformatting are inevitable when an email passes through various email gateways; adopting this unforgiving algorithm becomes difficult in such real-world email environments.
A no-fuss solution to this is to adopt the relaxed algorithm for the header while keeping the body canonicalization simple.
How to Implement DKIM Canonicalization?
Before we get into the process, remember that maintaining the integrity and trustworthiness of your email communications is not a one-and-done process but a continual one that requires regular reviews and updates as technology and standards evolve.
Here’s a step-by-step approach that you can follow to implement canonicalization effectively:
Look into your Current Configurations
The first step of implementing canonicalization is auditing your current email setup. This includes identifying which canonicalization method (simple or relaxed) is currently being used for both the headers and the body of your emails.
Modify Canonicalization Settings
Once you have reviewed your current configurations, the second step is to make adjustments to them. In this step, change the header canonicalization from simple to relaxed to make room for minor modifications without causing DKIM checks to fail. Here, you can also decide if you want to adjust the body canonicalization.
Test the Configurations
Before rolling out the updates for all your outbound emails, ensure that you run new canonicalization settings on a small batch of emails. Also, make sure to include various content types and formats to better understand the impact of the changes.
Monitor and Validate
After you implement the new configuration across all your emails, monitor the delivery rates and check for any DKIM failure reports. This will help you verify that the changes you recently made align with your email deliverability and integrity goals.
Now that you know that implementing DKIM and properly setting up canonicalization can go a long way in protecting against email spoofing and tampering while reiterating its trustworthiness, it’s time to take proactive action!
Still feeling overwhelmed by all the steps involved in DKIM canonicalization? While it is not as complex as it sounds, it is important to be careful when implementing these steps.
You can trust our team of experts at DuoCircle to enhance the integrity and trustworthiness of your email communications, ensuring they are protected against tampering and spoofing attacks.
Ready to make email authentication a breeze? Get in touch with us to discover all about our services and how they can bolster your email security, ensuring efficient management of your email systems.