Despite being aware of the various cyber risks, small businesses choose to ignore the need for a robust cybersecurity posture. They believe malicious actors only target large organizations and not them. However, lack of phishing protection or a business continuity strategy in the event of a cyber-attack leaves them at high risk. These cyberattacks can cost a business dearly if the IT security teams do not have an effective cybersecurity policy. The primary step in this direction is to address the challenges and vulnerabilities characteristic of an SME environment.
Types Of Threats That SMEs Face
An SME can face any cyber attack at any time. Many different types of threats and vulnerabilities expose an SME to losses, as discussed below.
- Automated Exploits: An automated exploit of vulnerability refers to the non-targeted attacks that affect the computer’s OS with a known security vulnerability. Most automated attacks target inherent vulnerabilities in the OS and occur if they don’t install the required patches. SMEs may not have adequate technical staff, and software may not be updated with the latest patch.
- Malicious HTML Email: These email attacks enter the system through an HTML email having a malicious site link, which is usually termed ‘phishing.’ When the user unintentionally clicks on the link, it triggers an automatic download of malware. Some email hosting providers offer inbound and outbound SMTP authentication to thwart such threats and ensure email security. Anti-phishing services can also protect SMEs from spear-phishing and other attacks, thereby making the entire business communication, including email forwarding and email archiving, secure.
- Unofficial Web Surfing: Employees can use the organization’s devices to access non-business-related sites. Such practices can infect the enterprise network with spyware, trojans, and malware. Additionally, employees who access social media sites from office terminals can expose the complete network to a malware attack. Restricting access and installing anti-malware software, including ransomware protection, can limit the damage caused by reckless surfing.
- Poor Security Configuration: The computing system’s security configuration of many SMEs could be at the default setting. Organizations need to change it and protect the system with robust security tools. Otherwise, it is easy for malicious actors to find the default credentials and log into the network resources.
Consequences Of A Data Breach
The consequences of a data breach on an SME can be both short-term and long-term.
Short-term Effects
- Penalties For Non-Compliance: Different regulatory bodies worldwide have defined regulatory cybersecurity standards for organizations. They fine them heavily in case of a data breach due to non-compliance to such regulations.
- Forensic Investigations: Another consequence of a data breach is that organizations will have to perform forensic investigations to determine an attack’s cause. While these investigations can bring valuable insights, they become costly for SMEs with a tight cybersecurity budget.
- Future Security Costs: An organization that underwent an attack needs to invest heavily in gaining back its customers’ trust. Additionally, if it doesn’t have backup facilities like MX backup, then the recovery costs escalate.
Long-term Consequences
Customers share confidential data with a business, thinking that the organization takes adequate security measures and their data stays safe. However, during a cyberattack, the data gets compromised, leading to a loss of trust in the brand.
Diminished reputation and loss of trust following a substantial data breach can have a long-term effect on any organization. Brand reputation is an SME’s most priced asset, and it must continuously work to maintain brand integrity. A single data breach episode can damage the best of reputations. Clients do not want to place their trust in an enterprise that has a shaky cybersecurity foundation.
Implementing A Robust Cybersecurity Posture In The SME Environment
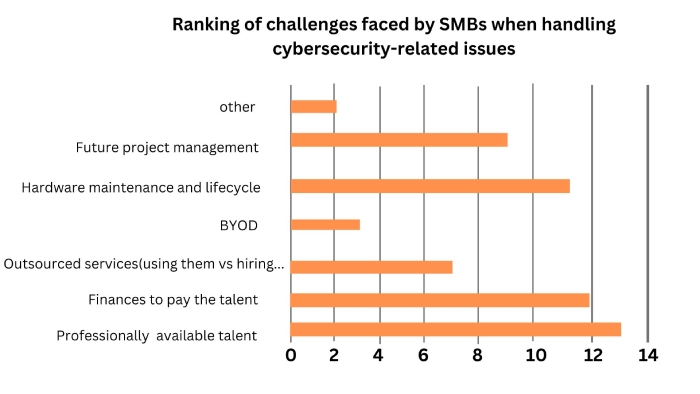
As per research by the Ponemon Institute, there has been a rise in the number of cyberattacks targeting small businesses. The same report mentions that out of 2,300 IT practitioners globally, 45% believed that their organization’s cybersecurity approach was ineffective. These developments make it clear that SMEs need to consider cybersecurity a top priority in the coming years. For implementing a robust cybersecurity posture, they need to overcome the following three key challenges.
- Cost Challenges: Unlike large enterprises, which have healthy IT budgets, SMEs often opt for cheaper choices with limited resources at their disposal. A typical example is a large enterprise that regularly carries out mock drills and invites ethical hackers to test their security systems using penetration tests. While these drills can provide useful insights into the inherent vulnerabilities, they are too expensive for a small business.
- Expertise Challenges: A lower cybersecurity budget of an SME directly translates to the limited ability to hire adequately skilled and experienced professionals. Most IT security teams in small firms lack cutting-edge skills, institutional knowledge, and broad experience. They cannot perform sophisticated and thorough cyber vulnerability assessments. The smart malicious actors leverage such vulnerabilities and launch sophisticated attacks that inefficient IT security teams fail to defend.
- Complexity Challenges: Cloud is the necessity of enterprises, big and small, who wish to collaborate efficiently. With increasing migration to the cloud and complex platforms, security teams must understand the specific challenges and added complexities of tenant migration and operating in sophisticated environments. However, smaller and inexperienced groups do not have the requisite know-how to achieve it.
Final Words
A cyber-attack can have devastating consequences for a small business. While larger enterprises may have adequate financial resources to recover from the negative PR and monetary losses, SMEs might not always be so lucky. Thus, an SMEs’ need of the hour is to consider a robust cybersecurity posture at the core of its policy-making.