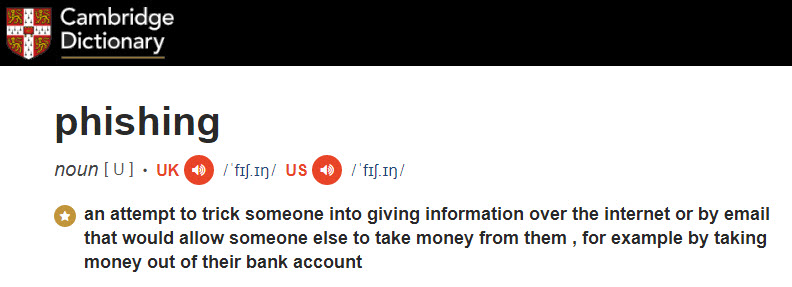
2018 was a good or bad year for phishing or phishing prevention depending on which side of the law you were on! Phishing is defined in many places on the internet, but I like the Cambridge Dictionary definition the best: “an attempt to trick someone into giving information over the internet or by email that would allow someone else to take money from them, for example by taking money out of their bank account”.
So, let’s see what the top phishing attacks were in 2018.
Account Verification
Table of Contents
This common type of phishing attack is that of account verification. Usually it is an innocent-looking email that seems like it comes from a major retailer or social network site (such as Facebook, Amazon, Walmart). It informs you that there is some problem concerning your account which you need to fix. The email has very convincing corporate logos and even sometimes list the company’s address and other such information to add an air of legitimacy to the charade. The email conveniently includes links so all you have to do is click on them. But in fact, the links take you to a fake website that looks very similar to the one you log into.
The criminal can then use your login information to access that website in order to commit fraud.
Google has instituted the Two-Step verification process to help protect users of its Gmail service. First you log into Google but then you are asked to verify you are who you say you are by performing another level of verification. This can take the form of entering a verification code sent to your mobile device or a security key which is inserted into a USB drive on your PC or laptop.
Sharing Files on the Cloud
Most everyone is familiar with sharing files on the cloud, whether for work purposes among colleagues or maybe to share photos with family members. In this scenario, the phishing attack uses well-known file storage companies such as Google Docs, Dropbox, Box.com, and Office 365 in order to convince the user to click on a link purportedly to a shared file. The end result is that your login information is stolen, or the laptop or computer is infected with a virus when the link is clicked.
Package Delivery
This phishing scheme is a favorite one especially during the holiday season. This type has been around for a long time. You receive an email notifying you about a package that is going to be delivered. Who doesn’t like to get packages? Even if you do not remember ordering something! The legitimate-looking email appears to come from a well-known delivery company such as DHL, UPS, or FedEx. Again, it conveniently gives you a link to click on, or an attachment which supposedly contains information about your order. When you click the link, you will be tricked into providing login information that a criminal can use, or by opening an attachment you infect your PC or laptop with a virus or other malware.
Tax Fraud
As if tax season is not bad enough, criminals have adopted a phishing scam to try to steal your money. This is especially apparent in the time frame leading up to April 15th of each year. Again, it takes form in an email seemingly coming from the IRS. It claims that you owe taxes, but it gives you a way out to avoid additional fines, legal action, or liens against your property.
Just remember that emails are not a method used by the IRS to collect alleged back taxes.
For more information about the IRS’s policies for communicating with you check out this link. (By the way, this IRS a legitimate link!). As a side note, there is ALSO a scam involving phone calls from law enforcement about collecting IRS debt. This is fake as well, and you know that for a fact when they tell you to go to a store and purchase a “Green Dot” card in the amount of the alleged debt. NOTE: Green Dot is a legitimate company and is just as much a victim as you are in terms of public relations.
Another related scam involved emails purported to come from a state accounting office or professional associations with accountants as members.The emails sought to obtain user names and passwords of accountants. In this way, the scammers could steal the information of the accountant’s clients as well as use that information to fraudulently file tax returns. In 2018 the IRS has seen email phishing scams directed at
- tax professionals,
- payroll professionals,
- human resources personnel,
- schools and
- individual tax payers.
One twist on the IRS scam is that when hackers use the victim’s real bank account to use direct deposit to deposit funds. Then the scammers use different methods to try to retrieve the funds. This can include fraudulent calls and emails claiming to represent collection agencies or the IRS itself. If you are the recipient of deposited funds you can see more information from the IRS on how to alleviate the situation legally. In addition, the IRS recommends that victims contact their financial institutions because in some cases, the affected bank accounts may need to be closed. This page gives instructions for direct deposited funds, or a paper check. And what to do if you have already cashed the check.
This website keeps a running list of corporate entities that have been victims of W2 phishing attacks just for 2018. Documents are available which give more detail about how the phishing attack took place and what the impact to the entity has been. Here is just a sampling of the documents:
The IRS offers additional help to combat phishing schemes. You can check out the phishing FAQ page on the IRS website.
Fake Invoices
This is another phishing attack which involves attachments. You receive an email saying that you or your company owe the amount on the attached invoice. Sometimes the email increases the urgency by claiming a certain service will be disconnected or threatening legal action due to nonpayment. As with other phishing attacks, clicking on the attachment can infect your PC or laptop with malware.
Compromised Mailchimp Accounts
The new year had only just started when virus watchers first noticed a phishing campaign using Mailchimp accounts that had been compromised to send out fake invoices.This scam used a zipped file containing some Javascript files which hid a malware app named GootkitInfostealer. Security experts think that the scammers used accounts that had weak passwords or has in some way been compromised. The scam appeared to run for three and a half months before dying down.
GDPR-Related Phishing Activity
Earlier this year, the European Union’s (EU) General Data Protection Regulation, or GDPR took effect. GDPR is a new regulation related to data protection and privacy for all members in the EU and the European Economic Area, or EEA. Its goal is to give individuals more control over their own personal data as well as simplify regulations for international companies doing business in the EU and EEA. By the way, you may have noticed a flurry of changes being made to terms and conditions by providers you deal with; this was because of the GDPR taking effect.
How did the scammers take advantage of this new regulation?
The implementation of the new law brought confusion with it and scammers used this as way to scam businesses with promises of information or with services that would help them deal with the new regulation.
Sextortion Scam
In this scam the hacker claims that he has hacked into your computer and stolen compromising photos or other information which he will send to family or friends or to your work place. That is, unless you pay a ransom for the information.
Sometimes the hacker asks for payment specifically in bitcoin.
The email may even have a password you have used just to make it sound true. The fact is that the hacker has probably matched up user names and passwords to you. However, even this does not mean you have been hacked. The scammer, knowing human nature, is banking on his victims to have incriminating photos or information on their computers.
Cryptocurrency
Over the last few years there has been an increase in the popularity of cryptocurrency and blockchain. Creators of new cryptocurrencies hold an Initial Coin Offering or ICO which is a crowdfunding event to raise money for the cryptocurrency. They provide an address for the crowdfunds to be sent to. However, because of this, criminals wanting to commit phishing fraud set up fake ICOs with any funds going to an address they control. So those who send money are scammed out of funds they think are going to a legitimate sales offering.
Political Campaigns
It seems like there are never-ending campaigns for this or that political office. In Russia, in March of 2018, scammers sent out fake emails to voters and promised some sort of reward just for filling out a survey in the email. Of course, they needed bank or credit card information in order to send the reward. As a result, the scammers were able to use the information to clean out their victims’ bank accounts or run up credit card purchases.
DocuSign
In a phishing attack using DocuSign, scammers send emails that look like they come from the DocuSign website. DocuSign is a service that allows individuals to electronically sign digital documents. Once you click on the email link you will be asked to sign into your email account. Once done, the scammers can invade your inbox.
Shortcut Attacks
In this attack, a hacker named TA505 sent out hundreds of thousands of emails with a unique attachment. It appeared to allow Windows 10 users the opportunity to create shortcuts to the different settings pages. The attachment was a PDF file with a PowerShell script that downloaded a trojan which allowed the hacker to have total access to that PC or laptop.
Here is a table showing the top phishing attacks, how many individuals and which companies were affected, what damage was done and what time period the attacks occurred in.
| Attack | How Many Individuals Affected | Which Businesses Affected | Amount of Damage | When Did the Attacks Occur |
| MailChimp | Jan-April, 2018 | |||
| Social Network | VKontakte | March, 2018 | ||
| Account Verification | Telegram | |||
| ICO | Bee Token | $85,000 | January, 2018 | |
| ICO | Buzzcoin | $15,000 | Quarter 1, 2018 | |
| Tax W2 | ||||
| Gmail Scam | 1 BILLION Google users targeted | Gmail.com | January, 2018 |
While it is not always easy to quantify the cost of a phishing scheme to a company, one estimate is that the average cost to a medium-sized company is $1.6 million per attack, which is way higher than implementing email security as a service in a company.
In Quarter 1, 2018 Kaspersky recorded the amount of spam to be 54% of all emails. In February it was 53% and in March it was 48%.
Also, in Quarter 1, 2018, the top ten malware groups found in email were:
Newest Phishing Scams for 2019
Android is the second most targeted platform by hackers after Windows. What we should expect in 2019 is more phishing attacks on mobile devices via text or voice.
Glossary
You have seen words or phrases dealing with phishing schemes in this blog which you may not know the meaning of. Here is a short list of the more common phrases:
Active Threat – A term for simulations using a recent phishing tactic or malware type that is new, frequent or potentially dangerous.
Attachment-based Phish – These are emails with what appear to be legitimate attachments, in different formats. But what they have in common is the ability to enable malware on your PC or laptop if opened.
CEO Fraud/Business Email Compromise (BEC) – The BEC is one of the most effective scams. The email appears to have come from an internal source or authority like someone requesting W2 information. It usually does not have any links or attachments which could trigger your PC or laptop’s malware or virus software. BEC scams targeted over 400 businesses per day last year, draining $3 million over the last three years.
Phishing Simulation – This is actually a simulation to test your users as to how to identify potential phishing schemes and learn the importance of protection from phishing service. It is merely a test and not the real thing.
Ransomware – This malware type is the most popular form today. It prevents or limits users from accessing their data, and then demands a ransom to unlock the frozen business operations. The average amount demanded after a ransomware attack is $1,077. More than 4,000 ransomware attacks occur every day.
Smishing–Just like other phishing schemes, this one targets hundreds or thousands of mobile devices with texts. There are different angles but the motive is to get as much personal information from the victim as it can.
Spear Phishing – This form of phishing scheme is a targeted one, meaning the scammer has some information about his victim which makes the attempt seem to be all the more legitimate. The information can be from a business that you trust like a bank, or a store where you have shopped.
Vishing – This form of phishing attempts to get personal information from you usually by phone. This information can take the form of PIN numbers, social security numbers, security codes on your credit card or passwords.
Whaling – also known as CEO Phishing.
What Should You Do About Phishing Scams?
The only reason phishing scams are still around is that people continue to get duped by them.
- First thing when you receive a suspicious email is check the address from whence it came. Sometimes that will give you a clue that all is not as it should be. Instead of clicking on links in an email, go to the website and log in that way. And do not be fooled by attachments as even Office documents and PDFs can have malware in them.
- Next beware of emails that have some sort of urgency to them which is a scheme mentioned previously mentioned in the Fake Invoices section of the blog.
- If you receive an email with a link supposedly going to a legitimate website, hover your mouse over the link. This will show you the full URL of where the link is trying to direct you. There is a website called http://www.getlinkinfo.com/ where you can enter the suspect URL to see if it truly goes to a legitimate website.
- Another clue is if the person to whom the email is addressed is a generic name like “Card Holder” or “Customer”. Finally, be wary of emails that contain mis spelled words or bad grammar. A legitimate company may have an occasional mis spelled word but not a lot that makes you take notice of it.
- To verify that a website is legitimate, check the spelling of the URL. A fake website may only be one character off from the real one and the scammer hopes you will not notice.
- In the URL field of a website, check to see if there is a locked padlock or key on the left of the URL. This is how your browser protects you from fraudulent websites.
- Also check to see if the address starts with “https:// instead of merely http://. The former indicates that the website is secure to use with confidence. The latter MAY indicate that the website may not be secure.
- Both Chrome and Firefox have built-in security that will notify you if you go to a website that contains malware, or if you have already downloaded actual malware.
All too often we hear about data breaches at companies, internet providers, retail stores, and social media websites. This is one way that scammers get lists of passwords. So, it would be fairly easy for a scammer to show you a single password you may have used in the past. The only time you should be concerned is if the password is one that you are currently using. If that is the case, then you should change that password immediately.
Here are some interesting statistics for 2018:
- 230,000 new malware samples are produced every day — and this is predicted to only keep growing.
- In 2016, the U.S government spent a whopping $28 billion on cyber-security – and this is expected to increase in 2017 – 2018.
- According to Microsoft, the potential cost of cyber-crime to the global community is a mind-boggling $500 billion, and a data breach will cost the average company about $3.8 million.
- According to data from Juniper Research, the average cost of a data breach will exceed $150 million by 2020 — and by 2019, cybercrime will cost businesses over $2 trillion — a four-fold increase from 2015.
- Ransomware attacks increased by 36 percent in 2017.
- One in 131 emails contains a malware.
- In 2017, 6.5 percent of people are victims of identity fraud — resulting in fraudsters defrauding people of about $16 billion.
- 43 percent of cyber attacks are aimed at small businesses.
- Unfilled cyber security jobs are expected to reach 3.5 million by 2021 — compared to about 1 million in 2016.
- According to billionaire investor Warren Buffett, cyber attacks is the BIGGEST threat to mankind — even more of a bigger threat than nuclear weapons.
- China is the country with the highest number of malware-infected computers in the world.
- 78 percent of people claim to know the risks that come with clicking unknown links in emails and yet still click these links.
- 90 percent of hackers cover their tracks by using encryption.
- It takes most business about 197 days to detect a breach on their network.
- Android is the second most targeted platform by hackers after Windows.
- 81 percent of data breach victims do not have a system in place to self-detect data breaches.
Conclusion
As technology evolves, hackers and scammers change their tactics. Individuals and businesses must be vigilant and protect themselves as much as possible from the threat.
References
Nine Major Phishing Attacks of 2018 (and How to Spot Them)
5 of the Most Notable Phishing Attacks of 2018… So Far
Sextortion Scam: What to Do If You Get the Latest Phishing Spam Demanding Bitcoin
Verizon 2018 Data Breach Investigations Report Tales of dirty deeds and unscrupulous activities.
Top Data Breaches of 2018: Hackers Find New Methods
55+ Companies and Counting Fall to W-2 Phishing Scams
Bigger than Ransomware, CryptoJacking is the new money maker
Report Phishing and Online Scams
Phishing Statistics: What Every Business Needs to Know
ENTERPRISE PHISHING RESILIENCY and DEFENSE REPORT 2017
How to Protect Yourself from Phishing Scams
The 2018 W-2 Phishing/BEC Victims List
What spear phishing is (with examples) and how can you avoid it
Common phishing scams and how to recognise and avoid them
100+ Terrifying Cybercrime and Cybersecurity Statistics & Trends [2018 EDITION]