![Google Admin Security, SharePoint File Theft, Health Department Cyberattacks – Cybersecurity News [April 08, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/what-is-a-dmarc.jpg)
by Brad Slavin | Apr 15, 2024 | Announcements
To stay ahead of threat actors and protect valuable assets, you must keep up with the latest cybersecurity news. Join us, and we’ll take you through this week’s discoveries with the new dual admin approval feature in Google Workspace, the new vulnerabilities in Microsoft SharePoint, how threat actors are targeting healthcare IT desks to steal finances, fake Facebook ads and pages spreading malware via hijacked AI tool pages, and the RUBYCARP botnet that has been operating for a decade. Stay Tuned!
(more…)

by Brad Slavin | Apr 12, 2024 | DMARC
DMARC has already gained the attention it deserves, owing to its efficiency in combatting phishing and spoofing attacks. But the journey wasn’t fast and steady from the beginning. It all started when SPF came into play, followed by the amalgamation of Yahoo’s DomainKeys and Cisco’s Identified Internet Mail (IIM). This blog covers the journey of all three email authentication protocols in detail.
(more…)
![Cyber Security vs Ethical Hacking: What’s the Difference?]()
by Brad Slavin | Apr 10, 2024 | Data Privacy
Are you struggling to safeguard your organization’s data from the plague caused by malicious attacks such as spoofing, DDoS, phishing, malware, etc.? In your pursuit of a secure and resilient future for your organization, we are sure you must have come across the term “cyber security strategy” quite often! Do you think it is just another buzzword, or does it carry real significance?
(more…)
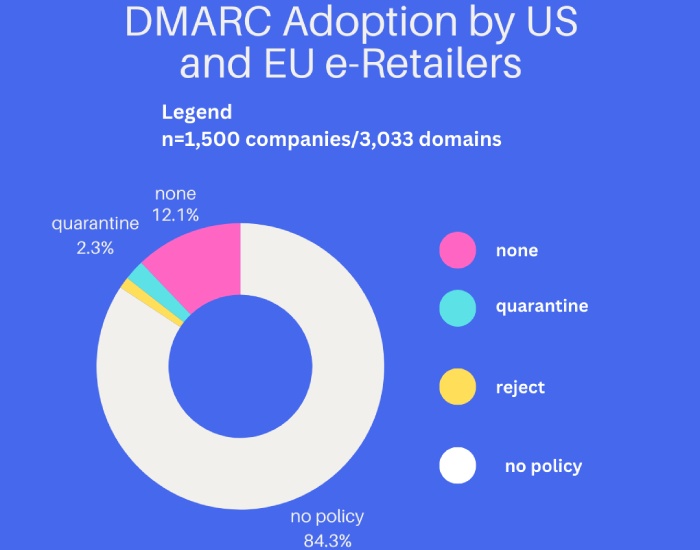
by Brad Slavin | Apr 9, 2024 | Email Security
Both these terms sound alike, so some people get confused and use them interchangeably. However, doing so isn’t right. DKIM, which stands for DomainKeys Identified Mail, is a successor to Yahoo’s DomainKey or DK.
(more…)
![Lama Security Breach, AT&T Security Lawsuit, Russian Card Theft – Cybersecurity News [April 01, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/Office-365-migration.jpg)
by Brad Slavin | Apr 8, 2024 | Announcements
We’re back with the latest cybersecurity scoop of the week. We’re here with the SurveyLama security incident, why AT&T is facing class action lawsuits, Russians charging individuals behind a 7-year card skimming campaign, how India freed 250 nationals being forced into cybercrime, and the latest JSOutProx malware strain that can steal your card details so you can avoid these threats.
(more…)
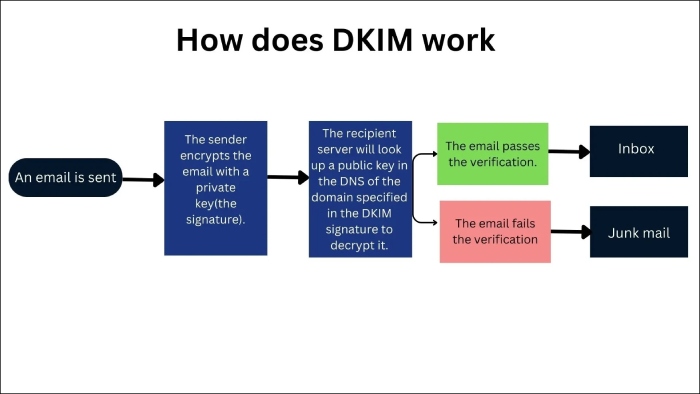
by Brad Slavin | Apr 5, 2024 | Email Security
Sometimes, Google Calendar invites don’t pass DMARC authentication checks because when the recipient replies to the invitation, the response is sent back through Google’s servers. Since the ‘From’ address and the originating servers don’t align, the Google Calendar invitation gets rejected as the sending domain’s DMARC policy instructs so.
(more…)

by Brad Slavin | Apr 4, 2024 | DMARC
Domain owners with multiple subdomains expose their businesses to phishing and spoofing attacks, which underscores the importance of protecting them with DMARC. Generally, domain administrators only deploy SPF, DKIM, and DMARC for the main domains, leaving unsecured subdomains to be the ideal entry points for threat actors. That’s why all your subdomains should have a quarantine or reject policy, with the percentage parameter ideally set to 100.
(more…)

by Brad Slavin | Apr 3, 2024 | Data Privacy
How do you stay one step ahead in a world where cybersecurity threats evolve faster than a click? One of the best ways to stay on top of your cybersecurity game is to cultivate a comprehensive understanding of the various determinants that shape the cybersecurity landscape—major threats, emerging technologies, regulatory changes, etc. And what better way to gain insights into all of this and more than by attending conferences?
(more…)
![Cyber Security vs Ethical Hacking: What’s the Difference?]()
by Brad Slavin | Apr 2, 2024 | DMARC
DMARC failure reports give insights into why emails failed DMARC checks and show where the trouble is to help you fix it. Invalid DMARC records fail to filter out phishing and spoofing emails. So, ensure your SPF and DKIM settings are correct, address alignment issues, and manage subdomains carefully.
(more…)
![Darcula Device Phishing, KuCoin AML Charges, Finland APT31 Culprits – Cybersecurity News [March 25, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/dmarc-generator.jpg)
by Brad Slavin | Apr 1, 2024 | Announcements
Here we are again with the latest in cybersecurity to help you keep up and stay a step ahead of threat actors and new scams. This week, we’ll share information about the Darcula phishing scheme targeting mobile devices, KuCoin’s failure to cope with the US AML requirements, the Finnish Police’s latest update on the parliament breach, the advanced PhaaS tool that bypasses MFA, and also how Google’s AI-powered search is promoting scam websites and malware. Let’s get into it.
(more…)
![Google Admin Security, SharePoint File Theft, Health Department Cyberattacks – Cybersecurity News [April 08, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/what-is-a-dmarc.jpg)


![Lama Security Breach, AT&T Security Lawsuit, Russian Card Theft – Cybersecurity News [April 01, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/Office-365-migration.jpg)



![Darcula Device Phishing, KuCoin AML Charges, Finland APT31 Culprits – Cybersecurity News [March 25, 2024]](https://www.duocircle.com/wp-content/uploads/2024/04/dmarc-generator.jpg)