Basics of DKIM syntax and tags
DKIM stands for DomainKeys Identified Mail, a cryptography-based email authentication protocol that helps receiving servers verify if an email sent from your domain was tampered with in transit. If you have DKIM deployed for your domain, then your server will affix a digital signature to the header with each outgoing email. This is a cryptographically secured signature that is produced using a private key that is known only to you. The counterpart of the private key is a public key, which is published in the DNS of your domain.
When the receiving server processes your email, it fetches the public key to confirm its authenticity and verify the message remained unaltered during transit.
Why is DKIM helpful to domain owners?
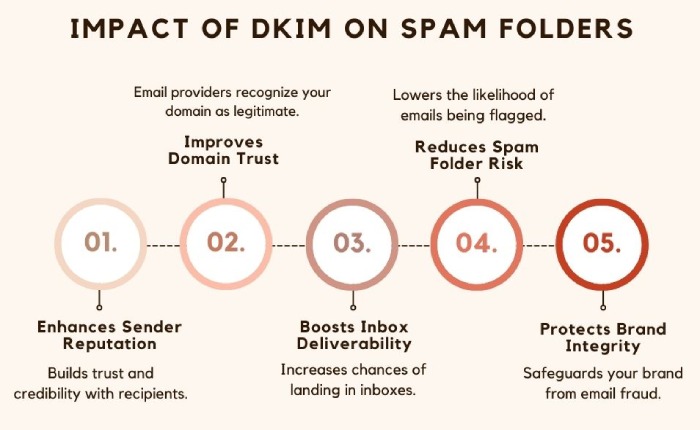
DKIM helps domain owners in their efforts to prevent their domain from getting involved in phishing and spoofing attacks. It basically verifies the legitimacy of outgoing emails. This keeps their brands out of financial and legal problems.
What else DKIM does is improve the sender’s reputation, which means mailboxes regard your domain as genuine and trusted. If this happens, most of the emails sent by you will land in the desired recipients’ inboxes instead of spam folders. Deploying DKIM is also mandatory compliance with many regulations, so if your brand falls under any of such compliances, you will need DKIM.
DKIM syntax
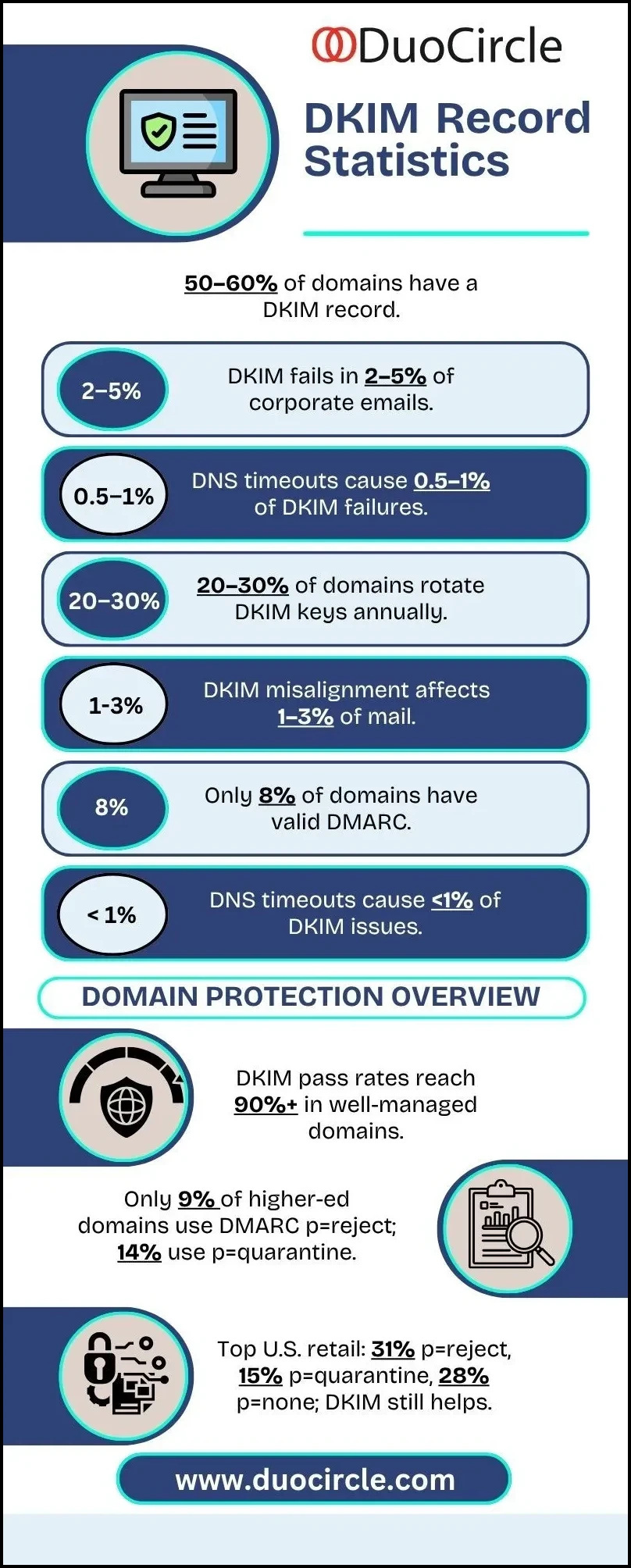
DKIM publishes the public key and associated information using a DNS TXT record. The record’s syntax comprises various tags, each serving a specific purpose. Below are the most common tags found in DKIM records:
- v: Denotes the DKIM version. Currently, the only version available is v=DKIM1.
- a: Indicates the algorithm used to generate the DKIM signature. Common values include rsa-sha256 and rsa-sha1.
- b: Represents the actual digital signature of the email headers and body, encoded as a base64 string and generated using the private key.
- bh: Stands for “body hash,” which is the hash of the canonicalized email body, encoded as a base64 value.
- c: Specifies the canonicalization algorithms applied to the header and body. Common options are simple/simple, relaxed/simple, and relaxed/relaxed.
- d: Refers to the domain name of the signing entity. If you’re creating the DKIM record, include your domain name here. Ensure the domain matches or is a subdomain of the one used in the ‘From’ header of your outgoing emails.
- h: Lists the signed header fields, separated by colons. For example, h=from:to:subject:date.
- i: An optional identity representing the user or agent on whose behalf the email is signed. For instance, i=user@eng.example.com.
- l: Known as the body length count tag, it indicates the number of body bytes included in the hash.
Final words
These DKIM tags convey essential information that enables the receiving server to verify the authenticity of emails sent from your domain. Therefore, it’s crucial to create your DKIM record with care. If you need assistance with email authentication, feel free to contact us or book a demo with DuoCircle for expert support.