Best practices to make Privileged Account and Session Management a breeze
Let’s ask you a pertinent question about your organization’s security.
Do you think that the accounts that manage your organization’s most critical systems and sensitive data are well protected?
If you have to think twice before answering this question, chances are that these might not be as secure as they should be.
The thing with privileged accounts is that these accounts hold the key to some of the most critical resources of your digital ecosystem, which means that if their security is compromised, your entire ecosystem will fall down. This is because unless you secure them properly, these accounts will become entry points for breaches, leading to data theft, operational disruptions, and reputational damages.
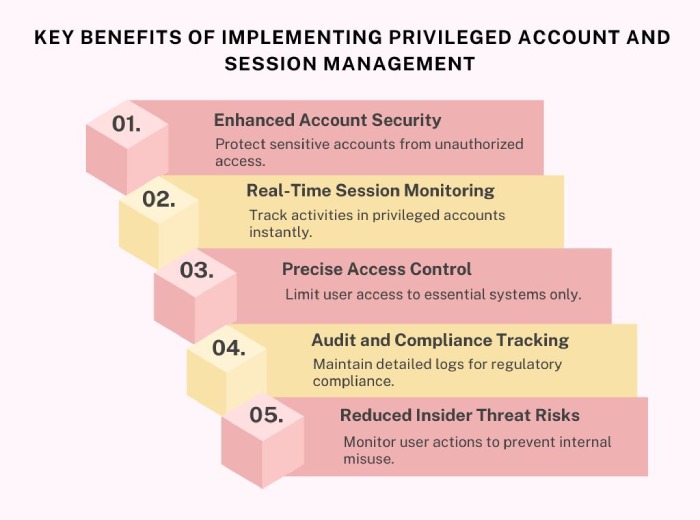
Let’s face it: managing privileged accounts is no easy feat. But by leveraging the right tools, you can make it easy and efficient. Privileged Account and Session Management (PASM) is a tool that simplifies the process of securing and managing these high-risk accounts.
In this article, we will understand more about this tool and look at some of the best practices that you can deploy to make privileged account and session management seamless and efficient.
What is PASM?
Privileged Account and Session Management is basically like a security guard for the organization’s most important accounts, which are the ones controlling essential systems such as DMARC settings or other sensitive tools. PASM helps ensure that only authorized and trusted people have access to these accounts, keeps their passwords safe, and tracks all activities whenever someone uses them. This way, PASM ensures that critical settings are kept safe and out of the hands of hackers or anyone who should not access them. After all, it is all about keeping your important systems safe and running smoothly.
Is PASM really necessary for your organization?
If your organization manages high-stakes systems and sensitive data, the answer is a resounding yes!
Let’s explain this to you in the context of email security and authentication protocols.
If you’ve authenticated your outgoing emails with SPF, DKIM, and DMARC, you’ve surely taken a step towards safeguarding your emails, but what about safeguarding the accounts that control and manage these protocols?
If you do not secure these privileged accounts, you’re basically leaving a critical gap in your security strategy for the cyberattackers to exploit. These are the accounts that manage your SPF, DKIM, and DMARC configurations, and if they fall into the wrong hands, an attacker could disable or manipulate your email authentication settings. This would not only ruin all your email protection efforts but also expose your organization to phishing attacks, domain spoofing, and reputational damage.
This is where Privileged Account and Session Management (PASM) becomes essential. Here’s why PASM really matters for your organization:
Preventing data breaches
With privileged accounts, what’s important is to secure all the sensitive information like customer data, financial records, intellectual property, or user credentials so that it does not get into the wrong hands. If it does, a lot can go wrong, like hackers could steal or leak customer data, leading to identity theft or fraud.
Avoiding operational disruptions
If the attackers invade your systems through any of the privileged accounts, you risk the chance of throwing off your organization’s most important operations. Since these accounts have access to the most critical data and systems, a single attempt at unauthorized access can lead to system outages, blocked email ecosystems, or locked resources.
If this happens, your employees might find themselves stuck as they would be unable to access the tools and information they need to do their jobs. You can also expect severe ripple effects of this mishappening. It will lead to customers losing trust in your brand or, even worse, losing valuable revenue opportunities.
Saving yourself from compliance issues
Compliance issues are among the worst things that could happen to your organization. Governing bodies like GDPR, CCPA, HIPAA, PCI-DSS, etc., are very strict about how your organization handles sensitive data, and if they spot any red flags, they might impose severe penalties, including hefty fines, legal consequences, and reputational damage. To stay compliant, it’s not just about securing privileged accounts — it’s also important to manage how user data is collected and used. That’s where consent management platforms come into play, helping you track and honor user privacy preferences in line with regulatory requirements.
The sheer struggle and the cost of getting out of these issues can be overwhelming and taxing. You obviously don’t want any of this, which is why it is crucial to take proactive steps to ensure compliance and protect your organization.
Preventing financial losses
Security incidents, such as data breaches or unauthorized access to critical systems, can lead to significant direct and indirect costs. As you know, any financial liability can take your organization ten steps backward and sometimes cause a huge dent, which is very difficult to recover from.
To prevent your organization from suffering the blow, you need to adopt robust security measures, especially for privileged accounts that control access to your most critical systems and sensitive data. Such accounts are usually the first choice for attackers, and their breaches can lead to huge expenses for system recovery, legal fees, regulatory fines, and even ransom payouts.
Protecting your brand’s reputation
Your brand is the reason your clients keep coming back to you, and if something compromises that trust, it can have long-lasting consequences. A security breach, especially that of privileged accounts, can leave a severe blow to your brand’s reputation. When sensitive customer data is leaked, or critical systems are compromised, it can create negative publicity and loss of confidence among customers, as well as bring down the market value.
What are the best practices that you should follow for effective privileged account and session management?
Privileged accounts are the core of your organization’s digital infrastructure. They control access to critical systems, sensitive data, and essential processes. You might have heard the saying that with great power comes great responsibility, but in cybersecurity circles, it comes with greater risks.
This is why it is important to manage these privileged accounts effectively. If you fail to do so, you might leave a door open to cyberattacks, data breaches, and operational disruptions.
So, how do you prevent this from happening? It starts with implementing practices that are aligned with your organization’s unique needs.
Let us take a look at some of them:
Automate the process of managing and discovering privileged accounts
First, identify all privileged accounts, including those that are unmanaged or overlooked. You simplify this process by using automated tools that discover these accounts, thereby reducing the chance of unauthorized activities slipping through the cracks. Once identified, they can be centrally managed— setting strong passwords, limiting access, and scheduling regular password changes. For accounts that manage critical systems like DMARC, automation ensures that your email security policies are protected and tamper-proof.
Limit access
Not everyone should have access to critical systems. It is a good idea to follow the principle of least privilege, which ensures that users and systems get only the minimum permissions they require to do their jobs, avoiding unauthorized changes and misuse. For instance, administrators should be granted privileges that only allow necessary access to DMARC, SPF, and DKIM settings for updates in order to limit exposure.
Protect privileged account passwords
Most people often choose weak passwords, thinking that they’d be easy to remember, but what they forget is that these passwords are also easier to crack. You cannot afford to take this kind of risk with privileged accounts. These accounts must rely on strong, secure passwords that are unique and hard-to-guess to prevent unauthorized access. Moreover, never reuse passwords across multiple accounts because if one account is compromised, all of them are at risk.
Another thing to keep in mind while managing privileged accounts is to rotate passwords regularly so that even if the credentials are exposed, they aren’t relevant to the attacker for long.
Opt for Multi-Factor Authentication (MFA)
If the stakes are so high (in the case of privileged accounts), passwords alone are not enough, as they can be stolen or guessed. Multi-Factor Authentication offers another layer of security by requiring multiple steps to prove a user’s identity; for instance, a user may have to enter a password followed by a code entered from the user’s phone. If an attacker happens to steal or obtain a password, they would not be able to log in if they do not have the second factor. Adding MFA to your privileged accounts makes it way harder for attackers to gain access to them and keeps your most critical systems more secure.
Monitor essential reports
Keeping an eye on what is going on behind the scenes is crucial for maintaining security, which is why you should monitor all the important reports. These reports can include minute yet crucial information on login attempts, access patterns, and changes to critical settings, provide valuable insights into how accounts are being used, and help detect any suspicious activity.
Even DMARC reports can help you identify unauthorized senders, diagnose misconfigurations, and prevent harm due to potential spoofed or phishing attacks against your organization and its stakeholders. After all, you don’t want to be caught off guard by such threats.